Adspect integration
Adspect is one of the best traffic filtering services. With Adspect you can detect bots and proxy/VPN traffic.
To perform the integration, you will need to install the Adspect module on your Binom server. Filtering criteria will be exactly the same, however all stats will be visible in Binom only (not in the Adspect panel).
Sign up for a subscription plan. Save 15% on any subscription plan with our Binom promo code.
Setting up Adspect
Adspect has to be installed on the same server with Binom.
Step 1
Connect to the server via SSH:
-
Connecting to the server
-
Windows
1. Download Putty
2. Run it, in the Host Name (or IP adress) field enter your server's IP, click Open
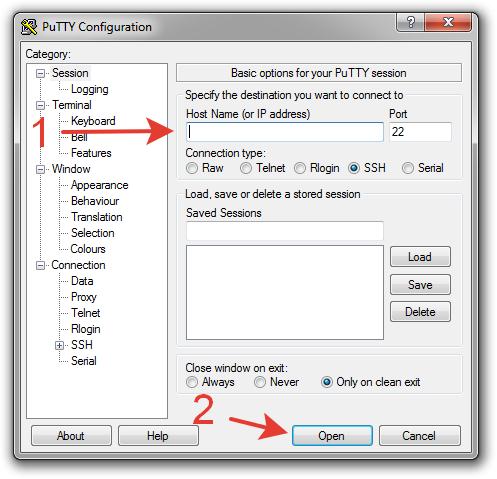
3. In the new window click Yes
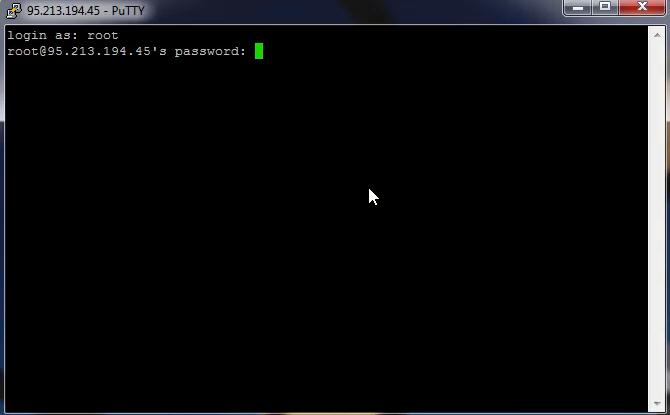
4. Enter your login and password (input characters will not be shown on the screen). You can simply copy your password and paste it into Putty by clicking the right mouse button:
-
Mac OS
1. Open Terminal
2. Execute:
login — your loginssh login@IP
IP — IP of your server
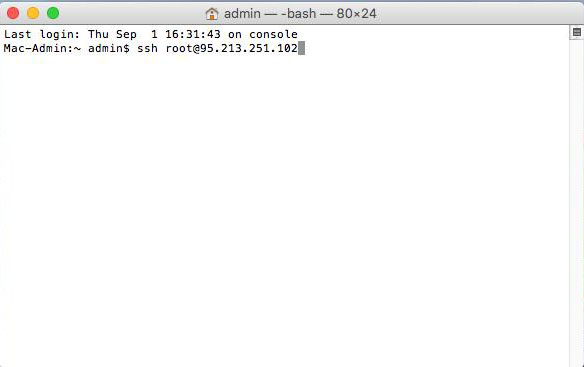
3. Type yes and press Enter
4. Enter SSH password (input characters will not be shown on the screen) and press Enter
-
Windows
Step 2
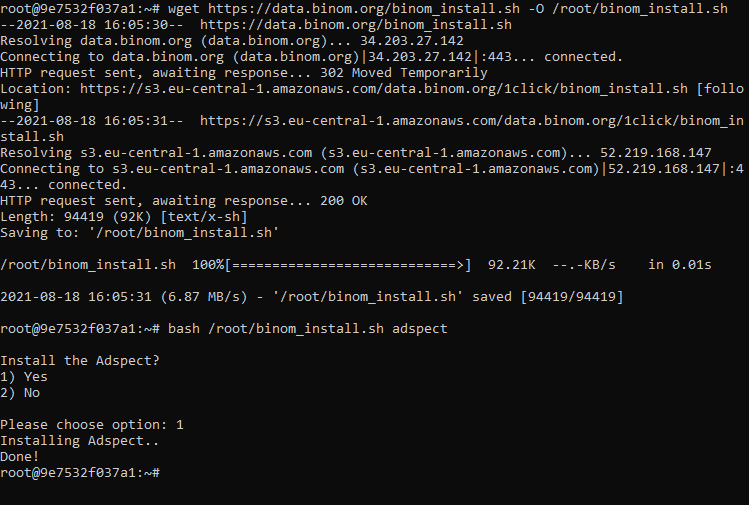
Download the latest version of Binom by executing:
wget https://data.binom.org/binom_install.sh -O /root/binom_install.shStep 3
Execute:
bash /root/binom_install.sh adspectStep 4
Type 1 and press Enter. In the end you will see Done!:
Keep in mind that this will slightly increase the load on the server.
Setting up Binom
Step 1
First of all go to your Adspect profile and see what your Account ID and API key are:
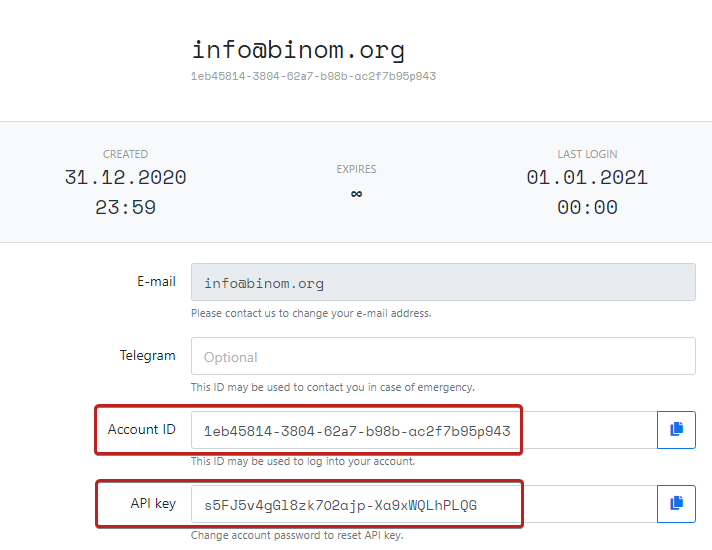
Go to your campaign settings and unroll the Protection menu. Check the Adspect box and click Add account.
In a new window appeared specify your Account ID и API key:
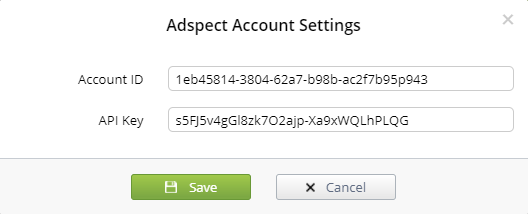
To change the account, go to Binom settings: Settings > API.
Step 2
Create the Bot rule. By using the Bot and NOT Bot rules you can define traffic as you like:
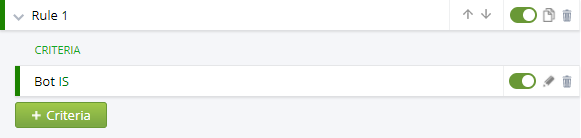
Step 3
When you turn on Adspect your JS Protection code will change, so make sure to update it.
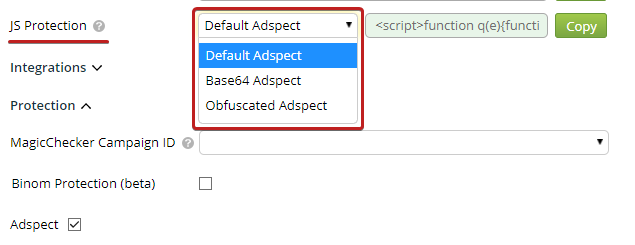
If you select the Obfuscated option, please note that it is best that your JS Protection code does not change within any one traffic source campaign. When a new obfuscated piece of code is generated, some values may get randomized and your traffic source might deem such changes in the page code suspicious.
Adspect integration can also be used together with Click API.
Checking bot detection
Here is how you can check if your Adspect integration has been enabled.
- — To check Adspect's primary bot filter, you can substitute your real IP with 8.8.8.8 using the HTTP header.
- — To check Adspect's Use fingerprint option (more info below), you can substitute your User Agent for one of a different browser than the one you are using (e.g., put in Mozilla Firefox UA when using Google Chrome).
Additional settings
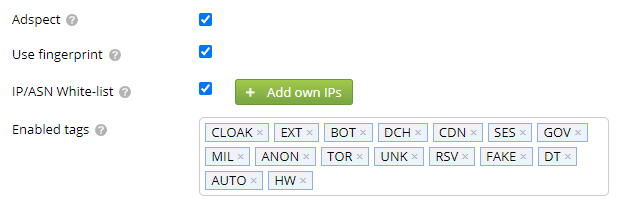
Use fingerprint
This option will turn on an additional traffic filter to make your bot detection even better.
IP/ASN White-list
The IP/ASN white-list field will allow you to add the IP and ASN (Autonomous System Number) exceptions.
If your ASN ranges are not working, check if you have whois installed on your server.
Enabled tags
The Enabled tags field allows to select tags that the tracker will be checking against when determining whether the click should be considered a bot.
In the Adspect tags column on the Clicklog tab you can see the exact tag that caused the click to be considered a bot by the Adspect.
-
Adspect tags
-
Please note that not all tags indicate that the click is fraudulent or is a bot.
Fraud — possibly fraudulent (not human) click.
False+ — a possibility of false-positive detection.
Tag Fraud False+ Description CLOAK Medium Low Cloaking-specific Adspect filters triggered EXT Medium Medium Cloaking-specific Adspect extended filters triggered BOT Yes Low Openly declared bot APP Medium No Click coming from or triggered by an application DCH High Low IP address belongs to datacenter, hosting company, or IP transit CDN High Low IP address belongs to CDN infrastructure SES Yes Low Search engine spider GOV Low Low Government institution MIL Low Low Military facility EDU Low Low University, college, school, or similar LIB Low Low Public library ANON High Low Public proxy, VPN service, or anonymizer TOR High Low Tor exit node UNK Yes Low Unmapped IP address (bogon) RSV Yes No Reserved IP address: local area network, class D, etc EMBED Medium No Embedding detected (<iframe>, <embed>, <object>, etc) FAKE High Low Browser is faking information about itself DT High No DevTools protocol is in use (web automation or develope tools) AUTO Yes No Web automation HW Medium Medium Highly suspicious hardware DATA Low No Missing or malformed fingerprint data (for POST requests) TOUCH Low Low Device has a touchscreen
-