Binom Protection
- Tracker settings
- VPN/Proxy detection block
- Bot detection block
- Reports and Clicklog info
- How to buy Binom Protect license
Binom Protection — is our complex anti-fraud detection solution.
Binom Protect can be used simultaneously with other integrations to detect bots. The click would be counted as a bot in case any service deems it a bot.
Binom Protection key features:
- Detecting VPN/Proxy and traffic from data centers
- Flexible bot detection mechanics
- In-depth reports and Clicklog information
- Extended fingerprints and risk scoring
Please, note that only Basic Binom Protection methods can be used at the moment together with:
- Click API (more info)
- LP Pixel (more info)
Tracker settings
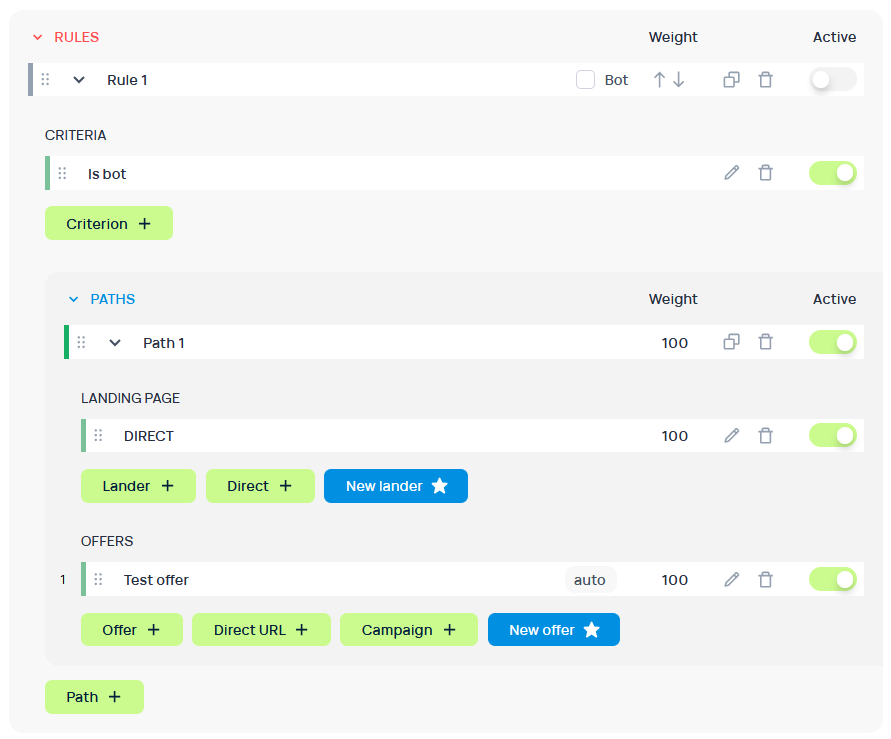
You can enable Binom Protection in the Binom Protect section of your Campaign settings.
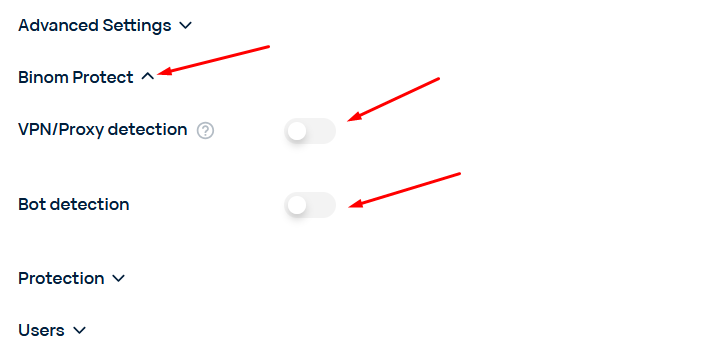
Binom Protect will mark the traffic as bot based on the selected tags. You need to create a Bot rule to send the clicks to a specific bot Path.
VPN/Proxy detection block
VPN/Proxy detection is a basic way to use Binom Protection.
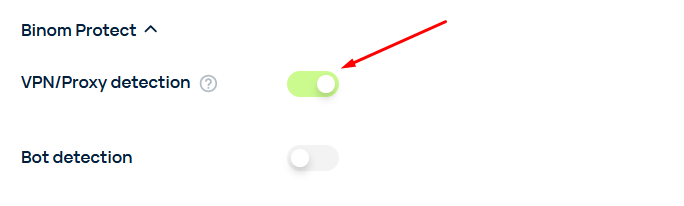
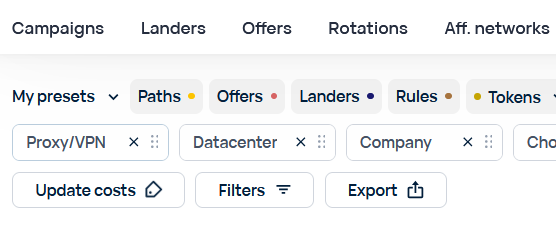
VPN/Proxy detection adds three new objects:
- VPN/Proxy - Detects traffic associated with known VPN providers, proxy, and TOR exit nodes.
- Datacenter - Detects traffic associated with known hosters (such as Amazon, Azure, Hetzner, etc..) as well as different SaaS organizations (including CDNs like Cloudflare, DDoS protection services, IP rental services, etc..).
- Company - Detects traffic associated with government, educational establishments, banks and other business organizations.
This info can be used as a rules criterion and can be accessed in the reports.
Bot detection block
Bot detection is an advanced and more flexible Binom Protection tool.
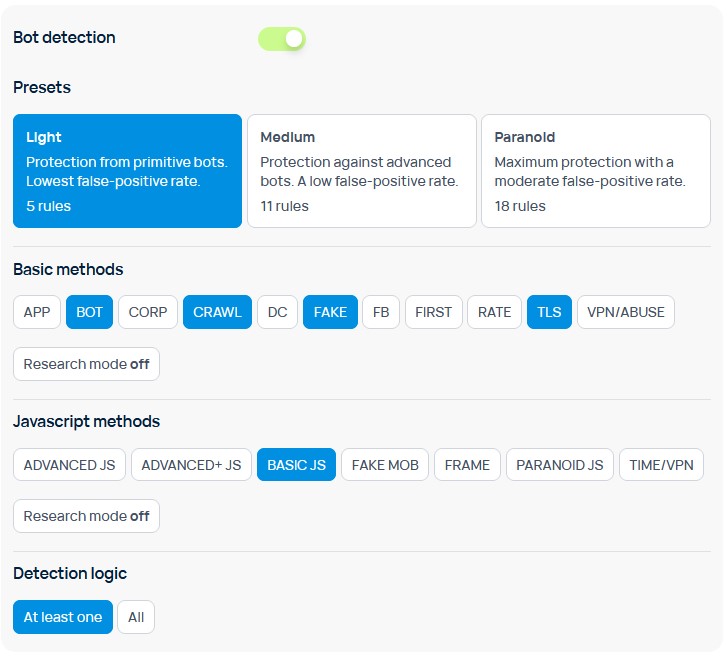
Presets - several presets:
Light - protection against primitive bots. The lowest chance of false-positive.
Medium - protection against advanced bots. Low chance of false-positive.
Paranoid - max protection. Moderate level of false-positive.
Basic methods - main methods of bot detection:
APP - Detecting Android and iOS app traffic. Useful to detect bots from malicious mobile apps that can open invisible Web View tabs on the device and do fake redirects.
Attention! Also filters out Web View browsers such as: Opera Mini, GX, Aloha Browser, etc..
Recommended using with caution.
BOT - Basic check to detect simple bots and known automated crawler bots through analyzing HTTP requests.
Filters out about 1-2% of the traffic.
Recommended to be used by default.
CORP - Module that checks the IP address against a database of different kinds of organizations: educational, governmental, bank, financial, and other business establishments.
Filters about 10-15% of the traffic on average.
Recommended to use with caution because it can be real traffic.
CRAWL - Module that checks the IP address against a database of classified known crawlers (search robots). Recommended to use if you don't want your link or site to be indexed.
DC - Module that checks the IP address against a database of known IP ranges of hostings. A lot of malicious traffic comes from them: bots that scan the network or parse the traffic source, bypassing of restrictions, traffic from personal VPNs or proxy servers, automated attacking traffic.
Filters around 5-10% of the traffic, geospecific.
Recommended to use with caution.
FAKE - Advanced check for inconsistencies of HTTP-headers in Chromium-based browsers. Can protect from GSB (Google Safe Browsing) ban in some cases.
Filters around 5% of the traffic.
Recommended to be used by default.
FB - Detects Facebook bots based on the HTTP headers and IP addresses.
Recommended to be used by default if you are working with Facebook.
Usage of this method is recommended to enhance the cloaking: https://docs.binom.org/utm-filtering-v2.php
FIRST - Used to fight off moderators in case the campaign is to be moderated and you need to send the first N clicks to the white page.
RATE - Aimed to fight clicks that come from the same IP and User Agent during a short period.
Filters around 5-10% of the traffic, but geospecific.
Recommended to be used by default.
TLS - Browser mismatch detection, based on TLS fingerprint.
VPN/ABUSE - Module checks the IP addresses against bases of IPs that were seen in malicious activity (spam, DDoS, fraud, hacking), belong to TOR networks, being proxy or VPNs from known providers (such as ExpressVPN, NordVPN, etc.).
Filters around 3-10% of the traffic, but is very geospecific.
Recommended to be used by default.
First visit clicks count - Sets a number of first clicks in the campaign that would be counted as bot. This setting can be used to fight off moderators.
First visit status - Sets a number of first clicks in the campaign that would be counted as bot. This setting can be used to fight off moderators.
Rate limit clicks count - Sets the amount of clicks and a timeframe. Any clicks that were made from the same IP and with the same User Agent exceeding the set amount would be counted as bots. For example, if you set the amount to "2" and a timeframe to 2 seconds, then from 3 clicks that came from the same IP and that had the same User Agent during the last 2 seconds, the first two would not be considered bots, but the third one would be a bot.
Rate limit time window - Sets the amount of clicks and a timeframe. Any clicks that were made from the same IP and with the same User Agent exceeding the set amount would be counted as bots. For example, if you set the amount to "2" and a timeframe to 2 seconds, then from 3 clicks that came from the same IP and that had the same User Agent during the last 2 seconds, the first two would not be considered bots, but the third one would be a bot.
Research mode - The tracker will check all incoming traffic in this campaign against all Basic methods, even if those methods are not enabled in the Basic methods block. This data will be used in reports, but clicks will not be marked as bots based on these checks.
If you want the tracker to mark clicks as bots, select specific methods in the Basic methods block.
Javascript methods - JavaScript-based methods of bot detection:
Take into consideration that all the following methods add a redirect. Use with caution if your traffic is vulnerable to delays and redirects
ADVANCED JS - Advanced detection based on the JS fingerprint of the device. Aimed to detect:
- spy services
- GSB (google safe browsing)
- anti-detect profiles of browsers on smartphones
- manipulations or substitution of browser or hardware specs
- patterns of browser action automatization
Filters 3-5% of the traffic, geospecific.
Recommended to be used by default.
ADVANCED+ JS - Advanced+ checks based on deep JS and network-layer fingerprinting of the client’s environment.
It typically filters 5% of traffic (geo- and vertical-dependent; can be higher on abuse-heavy segments).
Recommended by default for high-risk flows.
BASIC JS - Basic checks for inconsistencies of the fingerprints of the declared and real browsers. Can protect from GSB (Google Safe Browsing) ban in some cases.
Filters 3-5% of the traffic on average.
Recommended to be used by default.
FAKE MOB - Advanced checks based on the JS fingerpring of the device, aimed exclusively at Android and iOS devices. Protects from the following:
- fake Apple devices (100% chance)
- mobile profiles of anti-detect browsers
- spy services
- antivirus crawlers
- can protect from the GSB (Google Safe Browsing) ban in some cases
- detects manipulations or substitution of browser or hardware specs
Can filter around 25% of the traffic, geospecific.
Recommended to use with caution.
FRAME - Check aimed at finding embedded elements such as iframes, embedes or objects.
Recommended to be used by default.
Paranoid JS - Paranoid checks based on exhaustive JS fingerprinting and strict capability/sensor verification.
It typically filters 8–15% of traffic (highly geo-, device-, and vertical-dependent; may spike on privacy-hardened segments).
Recommended for high-risk flows only or as an escalation tier after Advanced+. Expect more false positives.
TIME/VPN - Check for inconsistency of IP address and time on the user's pc or device. A strong indicator of VPN usage.
Filters 1% of the traffic.
Research mode - The tracker will check all incoming traffic in this campaign against all Javascript methods, even if those methods are not enabled in the Javascript methods block. This data will be used in reports, but clicks will not be marked as bots based on these checks.
If you want the tracker to mark clicks as bots, select specific methods in the Javascript methods block.
Detection logic:
At least one - A click will be marked as a bot if it matches at least one of the Basic or JS methods you enabled above.
All - A click will be marked as a bot if it matches all of the Basic or JS methods you enabled above.
Reports and Clicklog info
Campaign reports and the Clicklog tab will provide you with info about the functioning of Binom Protection.
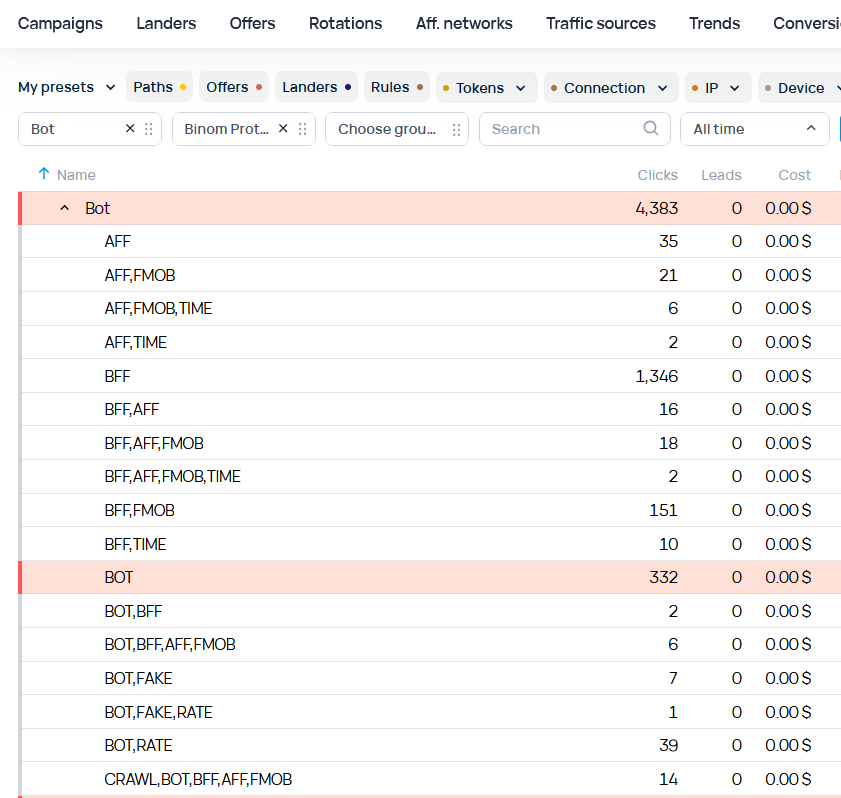
Both Reports and Clicklog can show you different tags for the same click that lead to this click being acknowledged as a bot.
How to buy Binom Protect license
One Binom Protect license will be applied to all the trackers on the same account.
In order to get Binom Protect license, navigate to your account over at binom.org.
Next, go to the Add/Renew Subscription section.
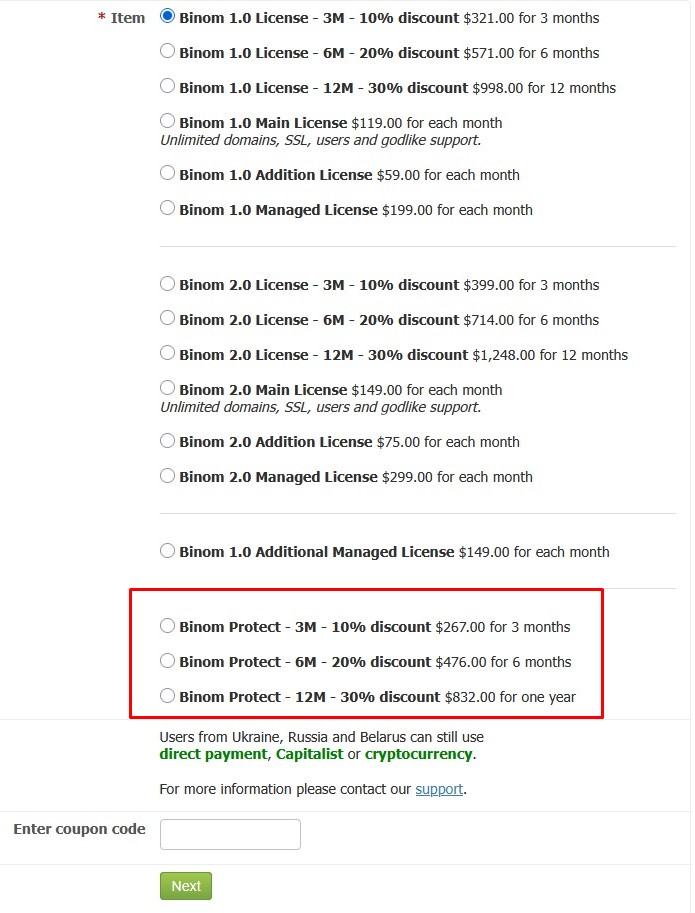
Choose the Binom Protect license type and the amount of days you want to get it for.
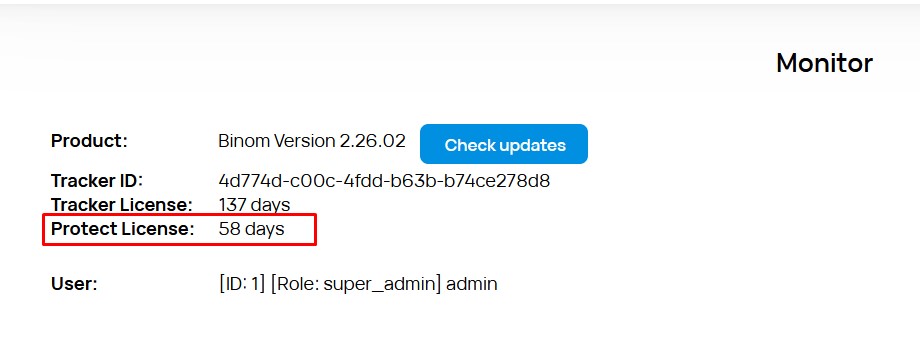
You can see the remaining Binom Protect license days on the Monitor tab in your tracker.