Google blacklist
If a campaign's or landing page's domain was blacklisted by Google, visitors following your URLs will see a warning window in their browsers. This affects your profit so connect Google Safe Browsing APIs and once every 20 minutes Binom will automatically perform the blacklist check for all your domains.
Enabling
Go to Settings > Stats and enter an API key from Google in the Google API key field.
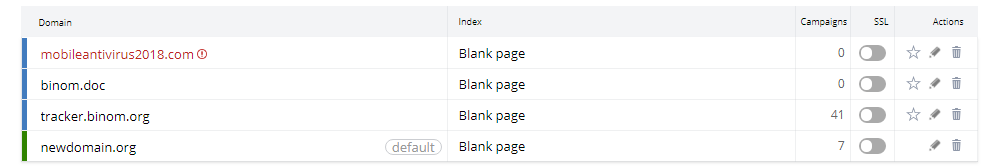
Blacklisted domains will be marked red:
Obtaining API key
To create an API key you need to have a Google Account.
Step 1
Open Google Cloud Platform, go to Dashboard > Create Project.
Step 2
Name your project (like Binom Domain Checker) and click Create.
Step 3
Open Safe Browsing API and click Enable.
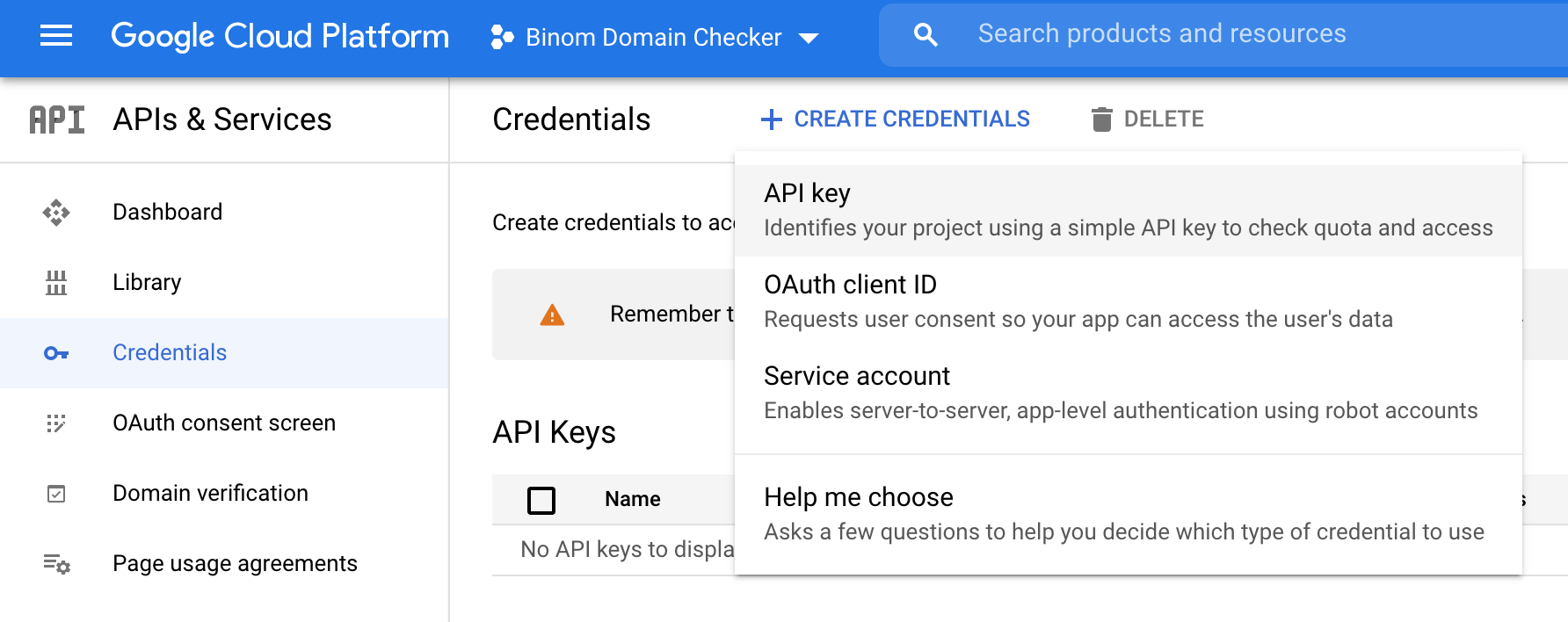
Step 4
To create the key, go to Credentials > Create Credentials > API key.
The API key will be shown in the new window appeared.
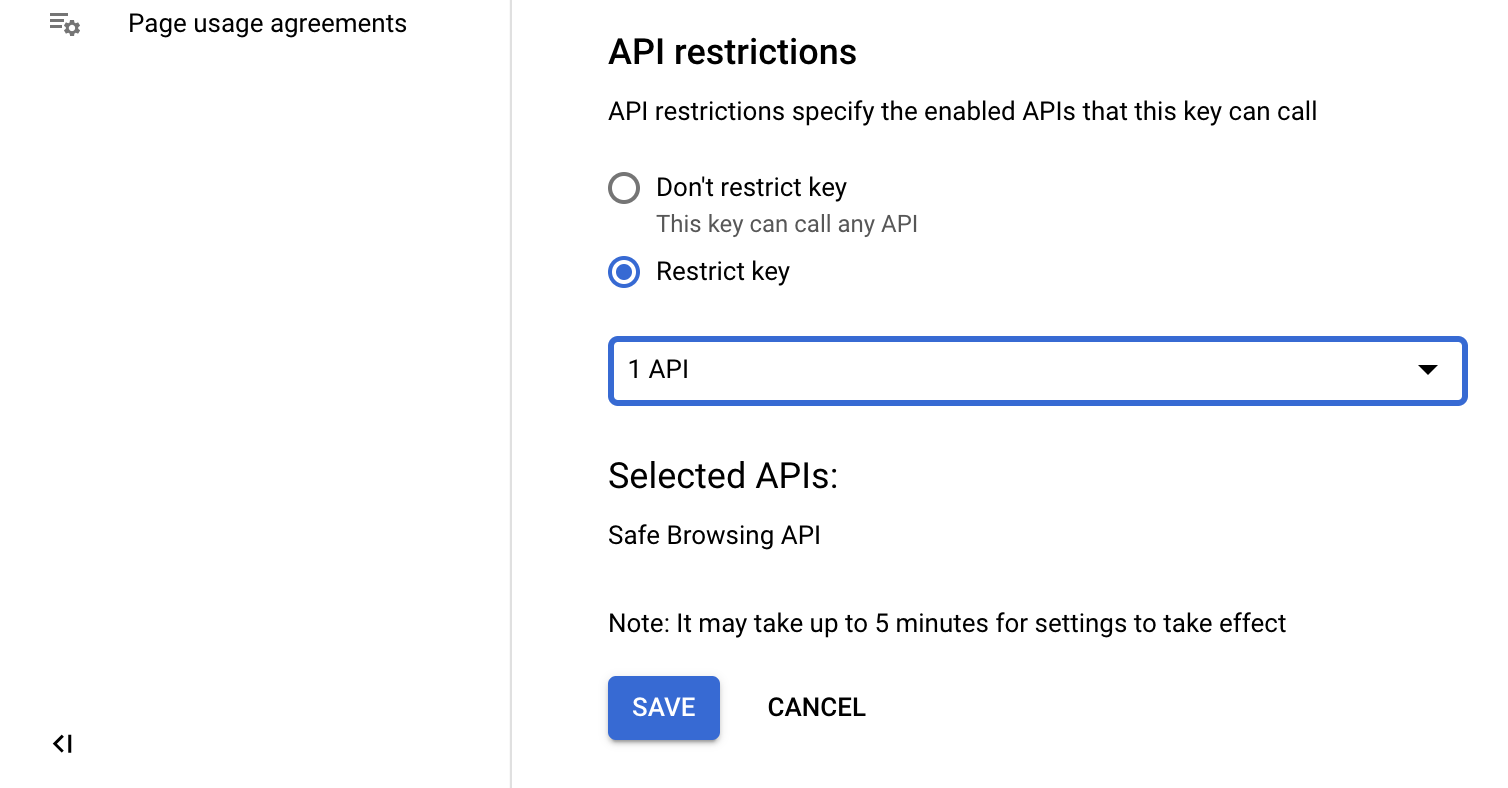
Step 5
Click Restrict Key to restrict the key — it will protect your account. Select Safe Browsing API from the dropdown menu and click Save:
Protecting your login domain
Sometimes your Binom login domain may get blacklisted by Google. We do not have precise information as to what might trigger Google to do so, but it could be related to abuse reports or domain/IP usage history. We also suspect being logged into your browser's Google account may play a role, as suspicious activity may be tracked by Google this way. In order to avoid such tracking, consider using anonymous browsers (such as this one).
Should your domain get banned, this is how your login page will look like:
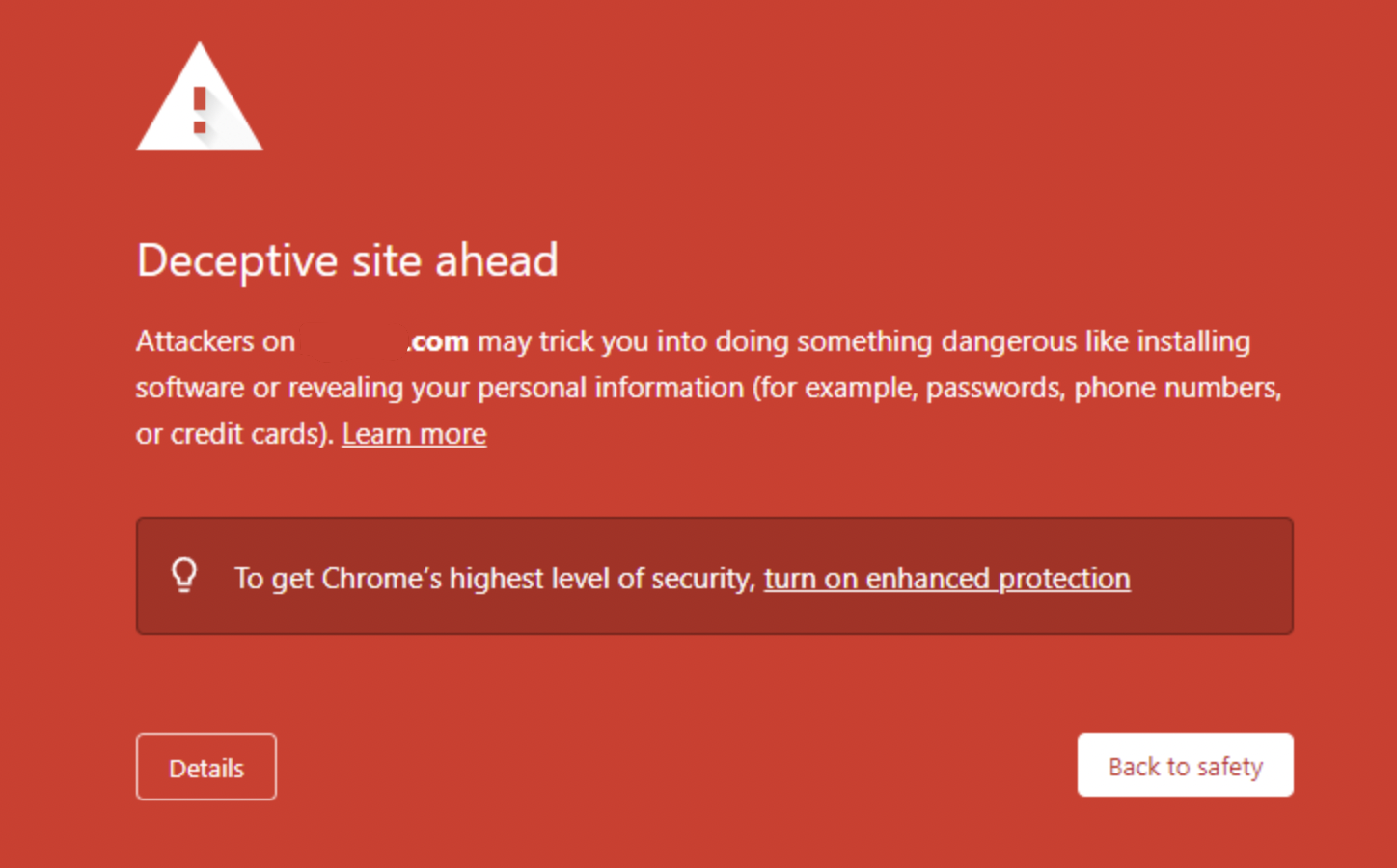
If you ever face this issue, the easiest workaround will be to simply ignore the warning message and proceed to the login page via Details. We recommend using additional domains for your campaigns, as login domain being banned does not usually affect any other tracking domains in use.
Using Nginx to restrict login page access
If you do not wish to simply ignore the message and are looking for an alternative solution, then you may select a new domain for login and restrict access to the login page on the web server level. Allowing only whitelisted IPs to access your login page usually helps to avoid new bans.
Step 1
The following domain configuration must go into /etc/nginx/sites-available/your-domain.com, where your-domain.com is your new login domain. In the code, replace domain and click_alias with the domain name and your customized click.php value respectively.
-
New domain configuration
-
server { listen 80; listen [::]:80; root /var/www/binom; index index.html index.php; try_files $uri $uri/ =404; server_name domain; access_log off; error_log /var/log/nginx/binom.error.log; # Binom url customization #error_page 404 = /click.php?type=404; location ~ \/(click_alias|click\.php|nlp\/) { try_files $uri/ @php; } location ~ \/(landers|\.well-known\/acme-challenge) { try_files $uri $uri/ =404; location ~ \.php$ { try_files $uri/ @php; } } location ~ \.php$ { include tracker-ips.conf; try_files $uri/ @php; } location ~ .* { include tracker-ips.conf; } error_page 403 =444 /444.html; location = /444.html { return 444; } location @php { fastcgi_split_path_info ^(.+\.php)(/.+)$; try_files $fastcgi_script_name =404; set $path_info $fastcgi_path_info; fastcgi_param PATH_INFO $path_info; fastcgi_index index.php; fastcgi_param SCRIPT_FILENAME $document_root$fastcgi_script_name; fastcgi_param QUERY_STRING $query_string; fastcgi_param REQUEST_METHOD $request_method; fastcgi_param CONTENT_TYPE $content_type; fastcgi_param CONTENT_LENGTH $content_length; fastcgi_param SCRIPT_NAME $fastcgi_script_name; fastcgi_param REQUEST_URI $request_uri; fastcgi_param DOCUMENT_URI $document_uri; fastcgi_param DOCUMENT_ROOT $document_root; fastcgi_param SERVER_PROTOCOL $server_protocol; fastcgi_param HTTPS $https if_not_empty; fastcgi_param GATEWAY_INTERFACE CGI/1.1; fastcgi_param SERVER_SOFTWARE nginx/$nginx_version; fastcgi_param REMOTE_ADDR $remote_addr; fastcgi_param REMOTE_PORT $remote_port; fastcgi_param SERVER_ADDR $server_addr; fastcgi_param SERVER_PORT $server_port; fastcgi_param SERVER_NAME $server_name; fastcgi_pass unix:/var/run/php/php7.4-fpm.sock; } ############### SSL Settings ############### listen 443 ssl; listen [::]:443 ssl; keepalive_timeout 60; ssl_certificate /etc/letsencrypt/live/domain/fullchain.pem; ssl_certificate_key /etc/letsencrypt/live/domain/privkey.pem; ssl_trusted_certificate /etc/letsencrypt/live/domain/chain.pem; ssl_ciphers EECDH:+AES256:-3DES:RSA+AES:RSA+3DES:!NULL:!RC4; ssl_prefer_server_ciphers on; ssl_protocols TLSv1 TLSv1.1 TLSv1.2; ssl_session_timeout 5m; ssl_session_cache shared:SSL:10m; ssl_stapling on; ssl_stapling_verify on; resolver 8.8.8.8 8.8.4.4 1.1.1.1; add_header Strict-Transport-Security "max-age=31536000"; ############################################ }
-
After that, reconfigure the rest of your active domains accordingly, otherwise any other domain will still be revealing your login page to unauthorized IPs.
Step 2
Next, you need to fill in your IP whitelist in /etc/nginx/tracker-ips.conf:
Step 3
After applying all the changes described above, reload the Nginx process to finish the web server reconfiguration: service nginx reload.
If you have any difficulty implementing the above steps, please reach out to our support team and we will be glad to help you.